Guest Blog: Cryptocurrencies, Money Laundering and Terrorist Financing
Cryptoassets and cryptocurrencies have been gaining in recognition and awareness in recent times. There are now more than 4,000 cryptocurrencies on the planet, of which Bitcoin is the most well known. Here is a chart of the bitcoin price over the last 12 months (source Coindesk), which shows an increase greater than the factor of six:
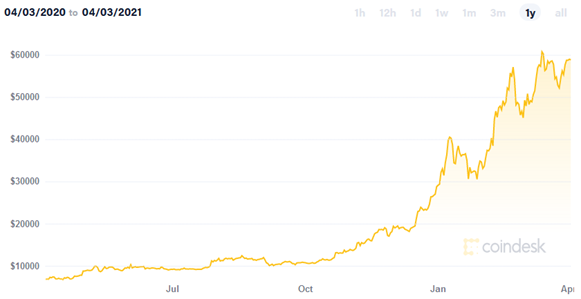
Despite this increasing popularity, is there a danger that cryptocurrencies can be used for illegal activities such as fraud, money laundering and terrorist financing?
At one end of the scale is the view that as all transactions occur on a blockchain platform and are visible to all, there is no chance of misuse. At the other end of the scale is the view that just as "where there's muck there's brass", the corollary applies, and someone will always find a way into a system, or to abuse a system. The answer lies somewhere in between.
Cryptocurrencies and Money Laundering
It is possible to obfuscate the ownership of cryptocurrencies, some of which have more privacy features than others. The market has not just seen the rise of cryptocurrency exchanges, but also of mixing and tumbling facilities by which cryptocurrencies are bundled, divided and redistributed amongst different accounts. This makes tracing harder to conduct, but not impossible, as displayed in a Canadian case in 2019 involving seizure of CAD 1.4m of bitcoin, and the seizure by US authorities in 2020 of a USD 1 billion Bitcoin wallet associated with the notorious Silk Road dark web criminal supermarket.
The Financial Action Task Force (FATF) released guidance on VASPs "Virtual Asset Service Providers" (known as Digital Assets in certain countries) in 2019.* Countries are now required to assess and mitigate their risks associated with virtual asset financial activities and providers; license or register providers and subject them to supervision or monitoring by their national authorities. VASPs are subject to the same relevant FATF measures as those that apply to financial institutions. The guidance addresses:
- How do virtual asset activities and VASPs fall within scope?
- How should countries apply the Recommendations in the context of virtual assets or VASPs?
- How do the Recommendations apply to VASPs and financial institutions?
The guidance also includes examples of national approaches to regulating and supervising VA activities and VASPs to prevent their misuse for ML and TF. Cryptoassets are developing rapidly and the FATF guidance was revised a year later.**
The report reviews implementation and sets out:
- how ML and TF risks and the virtual asset market have changed since June 2019;
- progress in implementing the revised Standards;
- the private sector's progress in implementing the revised Standards, including the development of technical solutions for the implementation of the "travel rule";
- issues with the revised Standards and Guidance; and
- next steps regarding virtual assets.
The report finds that both public and private sectors have made progress in implementing the revised Standards. 35 of 54 jurisdictions advised they have now implemented the revised Standards, with 32 of these regulating VASPs and three prohibiting their operation. The other 19 jurisdictions have not yet implemented the revised Standards. While supervision of VASPs and implementation of AML/CFT obligations by VASPs is generally nascent, there is progress. In particular, there has been development of technological solutions to enable the implementation of the "travel rule" for VASPs, even though there remain issues to be addressed by public and private sectors.
The VA sector is fast-moving which means continued engagement between public and private sectors is necessary. FATF has agreed to continue its focus on virtual assets:
- continue enhanced monitoring of VAs and VASPs and undertake a second review of implementation of the revised FATF Standards by June 2021;
- release updated Guidance on VAs and VASPs, addressing stablecoins, anonymous P2P transactions and travel rule implementation;
- promote understanding of ML and TF risks involved in VA transactions and potential misuse of VAs for ML and TF purposes;
- enhance its engagement with the private sector, including VASPs, technology providers, technical experts and academics, through its Virtual Assets Contact Group; and
- continue its program of work to enhance international cooperation.
Cryptocurrencies and Terrorist Financing
Terrorist financing is a different issue to money laundering. It does not cost much to create a significant terrorist incident. The Bali bombing of 2002 killed just over 200 people. The cost for the terrorists to mount the operation was estimated at AUD 25,000 (about GBP 14,000). The attacks in the US in September 2001 killed nearly 3,000 and caused insurance losses of around USD 40 billion. The cost to mount the operation was estimated at USD 400-500,000. The costs of the "War on Terror" since are put at USD 6 trillion. This is just the cost to the US economy.
There is evidence that terrorists are now using cryptocurrencies to finance their operations. Last September French police arrested 29 suspected members of a Syrian related terrorist gang and charged eight of them with terrorist financing. French counter terrorism police alleged widespread anonymous purchase of cryptocurrency coupons from tobacconists across France, which were then credited to accounts opened from abroad by jihadists, who were then responsible for converting them into cryptocurrency on bitcoin purchasing platforms. France as a result has announced compulsory KYC requirements for all crypto companies operating in France, including companies not based in the country. Crypto-to-crypto exchanges will also have to be registered.
Red Flags
So how can you try and spot the misuse of cryptocurrencies? There are a number of red flags to look out for on transactions, which, depending on the circumstances, may lead you to develop a suspicion as to the true provenance of the value involved in a transaction, or the true activities of those involved. Here are the indicators developed by FINTRAC, the Canadian FIU, as an example (taken in isolation, these may be innocent of course, or there may be another legitimate explanation involved):
It is important to note that depending on your business activities, some of these ML/TF indicators may not apply.
- Client portfolio only consists of privacy coins or has a high value in privacy coins (For example, Monero, Dash, Zcash)
- Client transfers Bitcoin in large volumes in exchange for privacy coins (For example Monero, Dash, Zcash, etc)
- Client is unwilling or unable to provide information about the source of privacy coins they once held or currently have
- Virtual currency addresses match addresses on recognized watch lists such as the list of the Office of Foreign Assets Control (OFAC) or law enforcement information
- Many individuals register with the exchange within a short period using a shared address, mobile device, phone number, IP addresses and other common identity indicators
- The client's virtual currency wallet or address is linked to fraudulent activity in media reports and/or cyber security bulletins
- A platform receives unusual or persistent requests from other exchanges/vendors/service providers in respect of a client's deposited funds
- A broker charges abnormally high commission fees compared to the industry standard
- The white paper is of poor quality, incomplete, misleading, and has limited information
- Publicity is created around the initial coin offering (ICO) (advertisements, celebrity endorsements, social media ads), also known as pump and dump ICOs
- The developers are anonymous or information provided about the ICO cannot be verified
- There is no access to the smart contract, to the code or to technical information about the token's creation
- There is no possibility to sell the investment or to exit the project to recover the invested funds
- A series of complicated transfers of funds to multiple addresses or wallets that seems to be an attempt to hide the source and intended use of the funds
- Transactions take place at the same time of day. Transfers from fiat to virtual currency and virtual currency to fiat
- High volume and frequency of transfers between different types of virtual currencies
- Client provides an anonymous email address obtained through an encrypted email service
- Funds are deposited or withdrawn from a virtual currency address or wallet with direct and indirect exposure links to known suspicious sources, including darknet marketplaces, mixing/tumbling services, questionable gambling sites, illegal activities (for example, ransomware) and/or theft reports
- Funds flow through a large number of intermediate addresses in a very short period of time prior to being deposited in a client's wallet, or just after being withdrawn
- Virtual currency passes through mixers/tumblers and is transferred to multiple wallets, where the funds are cashed out
- The virtual currency's funds originated from an over the counter trade broker that advertises its services as privacy-oriented/anonymous
- Virtual currency address has links or hops from a wallet address that has appeared on online platforms indicating support for violent extremism or radicalization (including social media, ads on fundraising sites, sites on TOR or messaging sites)
- The source of funds used for the purchase of large amounts of virtual currencies is unknown
- The email address used in the transaction is linked to advertisements for the sale of virtual currencies on peer to peer exchange platforms. These advertisements may suggest that the client is buying and selling virtual currency on a commercial scale through a business as a non-registered money services business
- The client frequently receives funds from multiple payment processors
- The client makes frequent payments or transfers to companies, post office mailing services or uses money orders from agents of the Crown for the purchase of computer software or hardware
Cryptoassets are here to stay, but just as with non cryptoassets there are good ones and ones which are not so good. Thus you need to assess how to differentiate between them, how each particular cryptoasset ecosystem works, how it can be abused, as well as how to select the ones which work best for you, and avoid getting caught up in cryptocrime.
* FATF Guidance on VASPs
** FATF Guidance on VASPs revised

